Top mistakes and actionable fixes for secure automation with self-questions to be asked to irrespective of roles illustrating the pitfalls and Solutions in Automation
Executive Summary
Automation has transformed how businesses develop, deploy, and operate systems — from CI/CD pipelines to RPA workflows, API-driven integrations, and autonomous infrastructure provisioning. However, the same automation that accelerates delivery can also accelerate compromise if not secured. This article outlines the most common cybersecurity pitfalls in automation, why they happen, and actionable solutions that technology leaders, architects, and engineers can implement. It is written from the lens of both a cybersecurity and automation expert, designed to help teams build secure-by-default automation.
Why This Matters Now
Automation has expanded from simple scripts to complex, multi-environment pipelines that span cloud, on-premises, and hybrid setups. With speed and scale come risks:
– Breaches propagate faster when triggered by automation.
– Misconfigurations are repeated at scale.
– Secrets and credentials can be exposed unintentionally.
– Vulnerabilities in automation tools themselves are exploited by attackers.
Approach for This Blog
Instead of simply listing mistakes and fixes, I will structure this through internal multiple-choice questioning to validate each point before including it. This ensures the content has depth and reflects paid-tier analysis quality.
Pitfall 1: Hardcoded Secrets in Automation Scripts
Self-question: Which is more dangerous in automation — hardcoded API keys or leaving credentials in CI/CD environment variables?
A) Hardcoded API keys in scripts.
B) Credentials stored in unsecured CI/CD variables.
C) Both are equally dangerous but in different contexts.
Answer & Analysis:
Hardcoding API keys in scripts is a direct exposure risk if the repository is public or compromised. Storing credentials in unsecured CI/CD variables risks exposure through logs or by unauthorized users with pipeline access.
Why This Happens:
– Developers prioritize speed over secure credential storage.
– Lack of integrated secret management tools.
Solution:
– Use centralized secret management tools.
– Enforce automated secret scanning in repositories.
– Rotate credentials regularly via policy.
Pitfall 2: Insecure Default Configurations in Automation Tools
Self-question: When deploying automation platforms, which is the greater risk?
A) Leaving default admin accounts enabled.
B) Not restricting network exposure of automation tools.
C) Both combined.
Answer & Analysis:
Default admin accounts provide immediate unauthorized access; open network exposure allows remote exploitation. Together, they amplify risk.
Why This Happens:
– Rushed deployments in proof-of-concept stages.
– Lack of post-installation hardening checklist.
Solution:
– Disable default accounts immediately.
– Bind automation tools to internal networks or use VPN-based access.
– Enable role-based access control (RBAC).
Pitfall 3: Lack of Access Segmentation in Automated Workflows
Self-question: Which practice is more dangerous in a multi-team automation environment?
A) Giving all automation jobs the same elevated privileges.
B) Assigning automation accounts without monitoring activity.
Answer & Analysis:
Overprivileged automation accounts create high-impact breaches if compromised. The principle of least privilege is often ignored for simplicity.
Why This Happens:
– Teams prefer one-size-fits-all service accounts.
– Misunderstanding of automation job scopes.
Solution:
– Apply least privilege to automation service accounts.
– Segment pipelines by function and environment.
– Audit account permissions quarterly.
You Should Also Read: automation testing interview questions
Pitfall 4: Ignoring Dependency and Library Vulnerabilities
Self-question: In secure automation, what’s the biggest risk from dependencies?
Answer & Analysis:
Automation often uses scripting languages that pull dependencies from public repositories. If unvetted, these can introduce malicious code or known vulnerabilities.
Why This Happens:
– Automation scripts are considered internal and assumed safe.
– Dependency updates are not part of automation governance.
Solution:
– Integrate Software Composition Analysis (SCA) tools in pipelines.
– Pin dependency versions and verify integrity. – Maintain an allowlist for external packages.
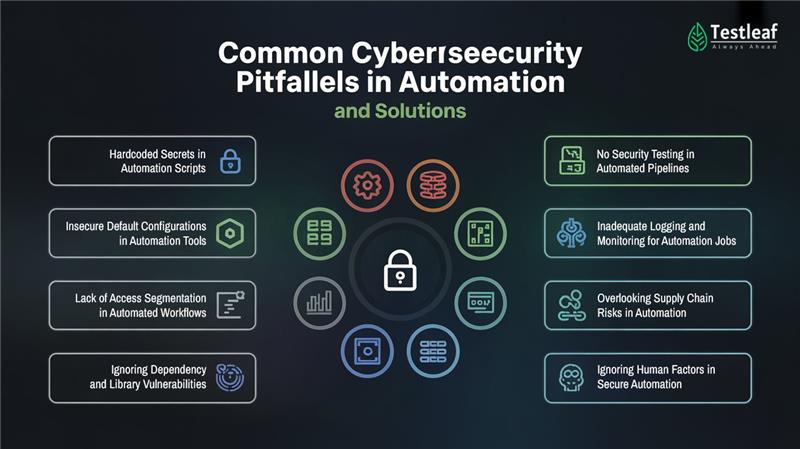
Pitfall 5: No Security Testing in Automated Pipelines
Self-question: Should security scanning be run in:
A) Only pre-production environments.
B) Every stage of the automation pipeline.
C) Only after code completion.
Answer & Analysis:
B. Security must be embedded at every stage (“shift left” security). Limiting it to pre-production misses early vulnerabilities.
Why This Happens:
– Perception that security tests slow down delivery.
– Lack of integration knowledge for security tools in CI/CD.
Solution:
– Automate static analysis (SAST), dynamic testing (DAST), and dependency checks in every pipeline run.
– Fail builds on critical security findings.
Pitfall 6: Inadequate Logging and Monitoring for Automation Jobs
Self-question: Which is worse for automation job monitoring?
A) Not enabling logs.
B) Logging without secure retention and alerting.
Answer & Analysis:
B. Having logs without monitoring or secure storage gives a false sense of security — attackers can erase evidence.
Why This Happens:
– Logging viewed as optional.
– Lack of centralized logging infrastructure.
Solution:
– Use centralized log aggregation with access control.
– Implement real-time alerting for automation anomalies.
– Protect logs from tampering.
Pitfall 7: Overlooking Supply Chain Risks in Automation
Self-question: In automation, which supply chain risk is more prevalent?
A) Compromised third-party plugins/extensions.
B) Malicious code in open-source automation templates.
Answer & Analysis: B is increasingly common due to the rise of malicious package uploads in public registries, but A can be equally damaging if plugins have wide access.
Why This Happens:
– Teams trust “popular” packages blindly.
– Lack of source verification policies.
Solution:
– Verify authenticity of all third-party components.
– Maintain a registry of approved automation templates.
– Regularly scan for supply chain vulnerabilities.
Other Helpful Articles: Top 10 Highest Paying Software Testing Jobs in India
Pitfall 8: Ignoring Human Factors in Secure Automation
Self-question: What’s the most common human factor failure?
A) Poor credential hygiene.
B) Social engineering targeting automation admins.
C) Both combined.
Answer & Analysis:
C. Social engineering can bypass technical controls entirely, and poor credential hygiene makes it easier for attackers to succeed.
Why This Happens:
– Limited security awareness among automation operators.
– No regular phishing simulations or security drills.
Solution:
– Conduct periodic security training for automation teams.
– Enforce strong authentication methods (MFA).
Building a Secure Automation Culture
Beyond the technical fixes, securing automation requires cultural alignment:
– Security is not an “add-on” but a built-in requirement.
– Leadership must sponsor security initiatives.
– Success is measured not just in delivery speed, but in secure delivery.
Action Plan for Leaders
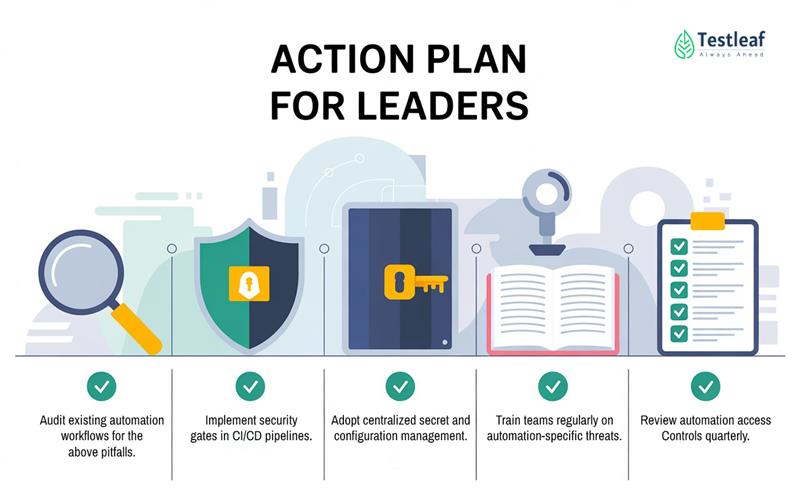
1. Audit existing automation workflows for the above pitfalls.
2. Implement security gates in CI/CD pipelines.
3. Adopt centralized secret and configuration management.
4. Train teams regularly on automation-specific threats.
5. Review automation access controls quarterly.
Conclusion
Automation can be your strongest operational advantage — or your fastest route to a breach. By identifying these common pitfalls and applying structured solutions, organizations can achieve secure, reliable, and compliant automation. The difference between successful automation teams and compromised ones lies in proactive security practices, not reactive patching.