As a QA engineer, one of the most nerve-wracking aspects of test automation used to be handling credentials. In the early days of our CI/CD pipelines, testers often used personal or shared accounts to execute automated tests. At first glance, it seemed convenient: everyone had access, and tests ran as expected. But over time, the risks became painfully clear.
- Personal credentials could be accidentally leaked in logs or reports.
- Shared credentials created security concerns and reduced accountability.
- Region-specific scenarios were difficult to test without exposing sensitive data.
These challenges weren’t just theoretical—they posed a real threat to our company and compliance obligations. That’s when we implemented Non-Warm Body (NWB) accounts, and it completely transformed how we approached test pipelines.
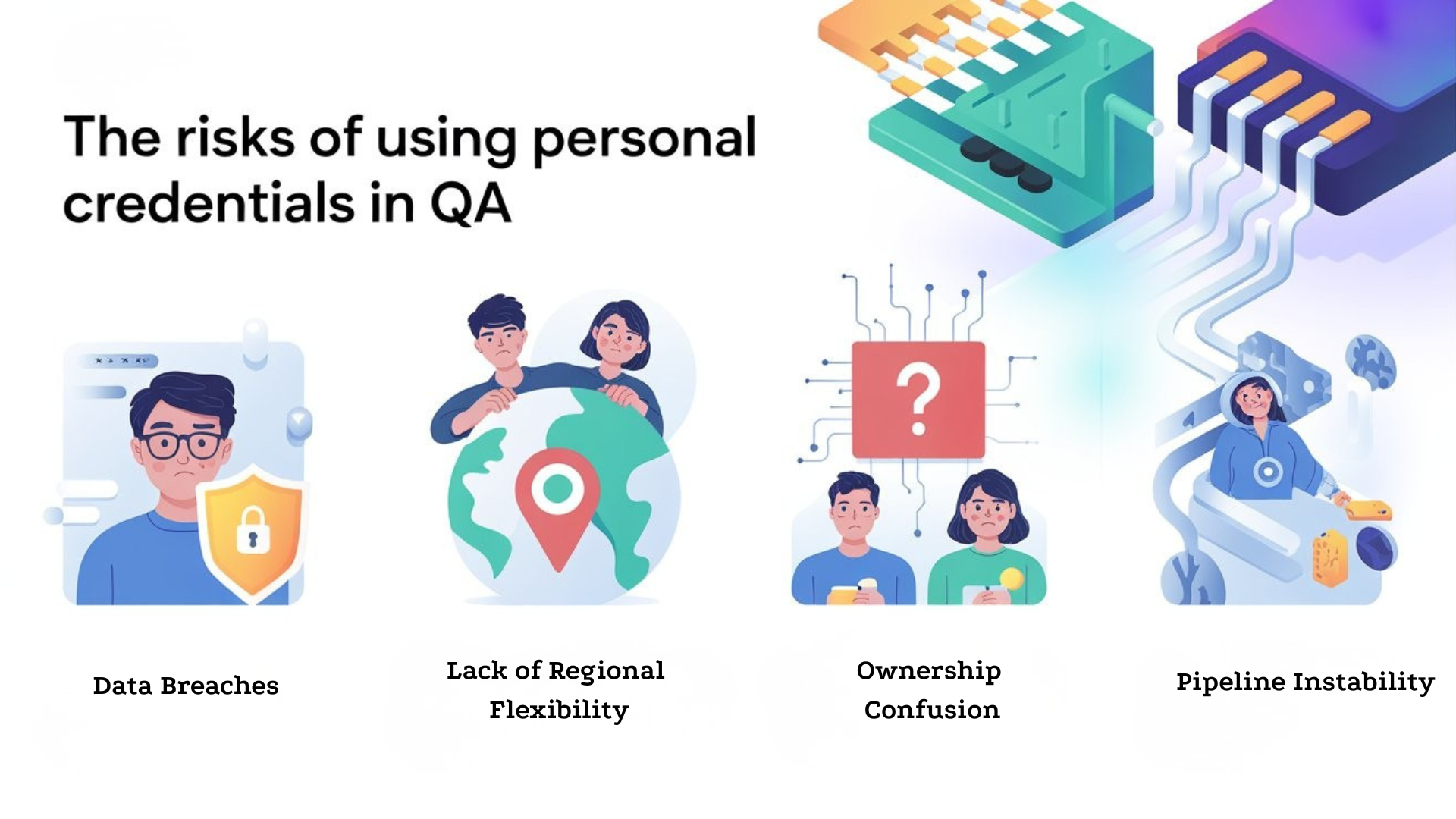
The Risks of Using Personal Credentials in QA
Before NWB accounts, our test setup had several critical risks:
1. Data Breaches
Personal credentials often ended up in pipeline logs, screenshots, or HAR files. Anyone with access to the CI/CD system could inadvertently see usernames, emails, or sensitive tokens. This was a ticking time bomb for data privacy and compliance.
2. Lack of Regional Flexibility
Our application had region-specific features, like banker profiles or payment gateways. Using personal accounts tied to one region meant tests could fail in other regions or accidentally use live production data, creating potential regulatory violations.
3. Ownership Confusion
Shared personal accounts made it difficult to track who ran which tests. If a test failed or caused data corruption, it was hard to assign accountability.
4. Pipeline Instability
Personal accounts were sometimes deactivated, passwords changed, or locked due to inactivity. Automated tests would then fail unpredictably, creating unnecessary noise in CI/CD pipelines.
Other Helpful Articles: automation testing interview questions
What Are NWB Accounts?
Non-Warm Body (NWB) accounts are dedicated test accounts that are managed independently of any individual tester. They are:
- Region-specific: Each account is configured for a specific region or environment.
- Non-personal: No real user credentials are used, reducing the risk of data exposure.
- Automated: Credentials are stored securely in the pipeline and injected during test execution.
- Ephemeral or Resettable: Accounts can be reset between runs, ensuring consistent test data.
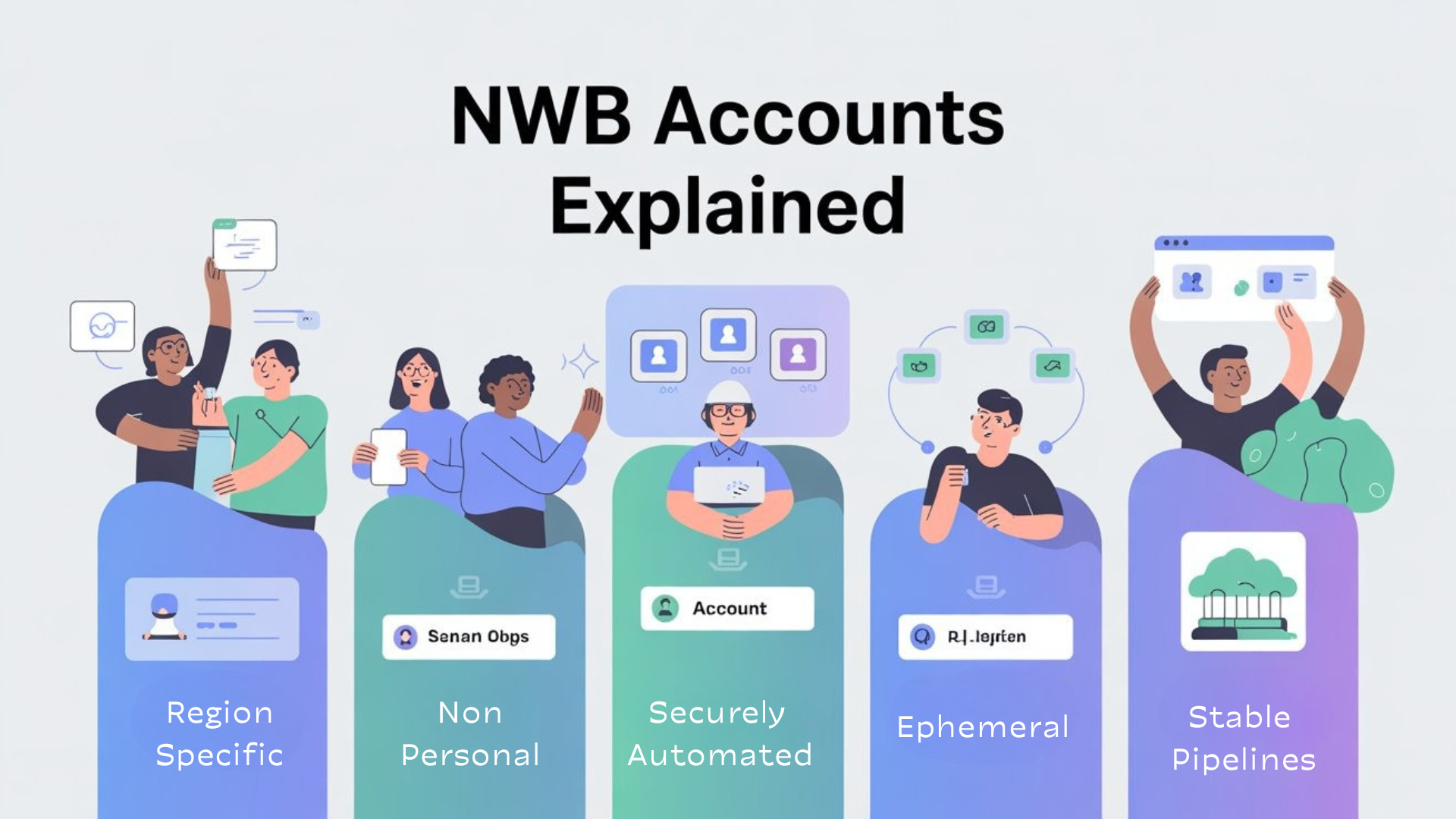
Essentially, NWB accounts allow us to run automation without touching real user data while maintaining full functionality across environments.
How We Implemented NWB Accounts
Introducing NWB accounts required both technical implementation and process alignment:
1. Identify Critical Scenarios
We first mapped test flows that previously used personal credentials. Priority was given to:
- Login and authentication tests
- Region-specific user flows
- Sensitive transactions (like debit/credit or balance validations)
2. Create Dedicated NWB Accounts
For each environment and region, we created dedicated test accounts with the following considerations:
- Unique username and password per environment
- Preloaded test data to simulate realistic scenarios
- Limited permissions to avoid affecting production or sensitive data
3. Secure Storage and Injection
Credentials were stored securely using pipeline secrets or vaults, not in code. During pipeline execution, the test framework would inject credentials dynamically. This ensured that no personal data was hard-coded or exposed in logs.
4. Integrate with CI/CD Pipeline
All NWB accounts were fully integrated into the CI/CD pipeline, enabling automated tests to use them without manual intervention. The pipeline now dynamically selected the correct account for the environment and region being tested.
5. Reset and Maintenance
To maintain consistency, NWB accounts were reset after each test run. Any test-created data was cleaned up, ensuring that each execution started from a known, stable state.
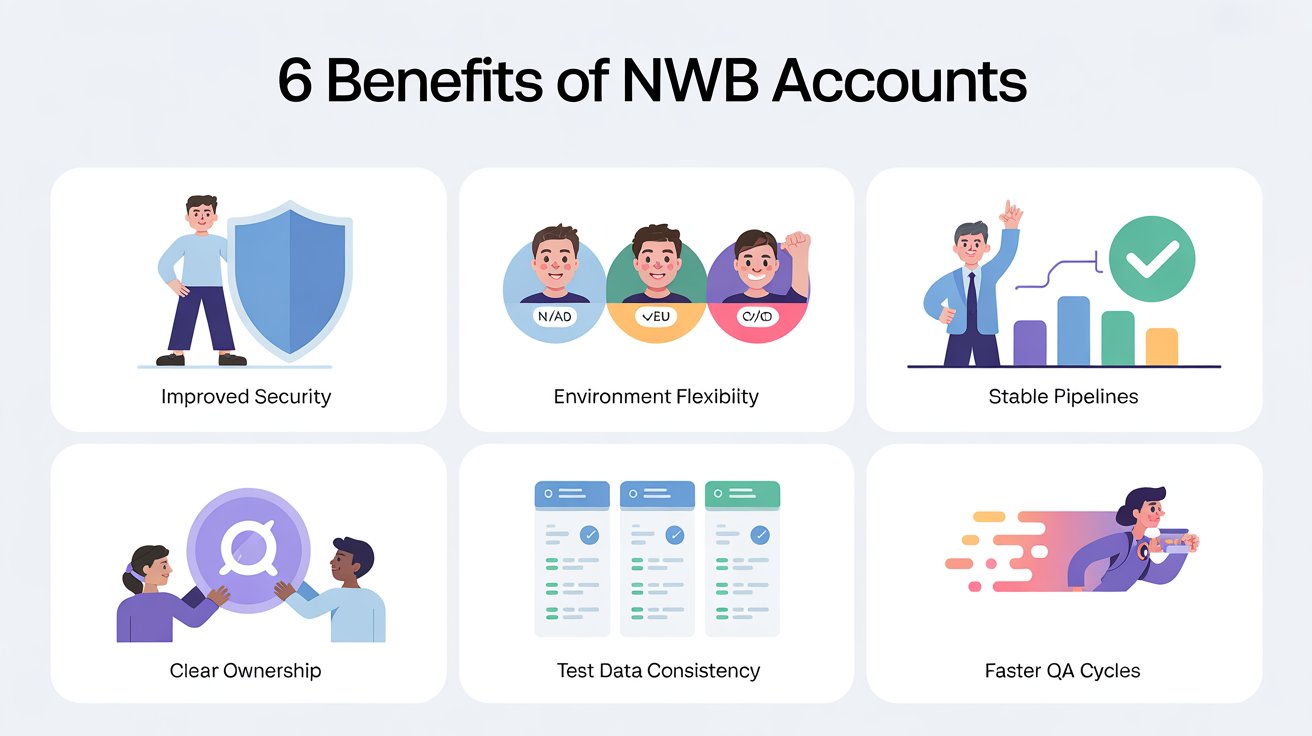
Benefits of NWB Accounts
Implementing NWB accounts brought tangible improvements to our QA process:
1. Improved Security
By eliminating personal credentials, we reduced the risk of data leaks in logs, reports, and dashboards. This was especially critical for sensitive user data and regulatory compliance.
2. Environment Flexibility
NWB accounts enabled testing across regions and environments without relying on individual testers’ credentials. Regional flows could now be validated consistently.
3. Stable Pipelines
No more failed tests due to deactivated or locked personal accounts. NWB accounts are managed centrally, providing predictable, reliable authentication in automated tests.
4. Clear Ownership
Pipeline logs now reference NWB accounts, not personal users. This makes it easier to track test executions, failures, and accountability, reducing confusion during troubleshooting.
5. Test Data Consistency
With resettable NWB accounts, each test run starts with clean and predictable data, improving reliability and reducing flaky tests caused by leftover data from previous runs.
6. Faster QA Cycles
Tests no longer fail due to credential issues, meaning fewer manual interventions and faster CI/CD feedback. The team could focus on quality testing, not pipeline firefighting.
Lessons Learned
1. Security Comes First
Automation is powerful, but it must respect data privacy and security. Personal credentials in pipelines are a risk, and NWB accounts mitigate that risk effectively.
2. Process + Technology
Implementing NWB accounts isn’t just a technical change; it requires aligned processes, including account creation, maintenance, and environment management.
3. Regional and Environment Awareness
Automation should reflect the complexity of the real system. NWB accounts enable testing across different regions and configurations, ensuring thorough coverage.
4. Reusability Matters
Once NWB accounts are set up correctly, they can be reused across pipelines, projects, and test suites, reducing maintenance overhead in the long run.
Continue Reading: playwright interview questions
Real Impact on Our QA Process
After implementing NWB accounts:
- Pipeline stability improved drastically; credential-related failures disappeared.
- Security and compliance concerns were alleviated; sensitive data was never exposed.
- Flaky tests due to login or authentication issues were eliminated, improving CI/CD trust.
- QA could execute region-specific flows confidently, knowing that NWB accounts were isolated and reset after each run.
- Stakeholders gained confidence in automated test results, as failures now reflected real application issues, not account mismanagement.
From my perspective, NWB accounts transformed QA from a reactive team constantly fighting false failures into a proactive, reliable pillar of quality assurance.
Conclusion
Using personal credentials in automated pipelines may seem convenient, but it’s risky, unreliable, and ultimately slows down QA. Implementing Non-Warm Body (NWB) accounts solves these problems by providing secure, region-specific, resettable test accounts.
From my experience, NWB accounts are more than just a technical improvement—they are a strategic enhancement that increases pipeline stability, reduces false failures, ensures compliance, and allows QA to focus on real quality issues.
For any QA or SDET team struggling with credential management, security concerns, or flaky tests caused by account issues, adopting NWB accounts is a game-changer. It’s smarter, safer, and ultimately enables faster, more reliable releases.
FAQs
Q1. What is an NWB account in QA testing?
An NWB (Non-Warm Body) account is a dedicated test account that is not tied to any real user. It’s created specifically for automated testing, managed centrally, and often region- or environment-specific. These accounts avoid using personal credentials while still allowing full end-to-end test coverage.
Q2. Why are personal credentials risky in CI/CD test pipelines?
Personal credentials can leak into logs, reports, screenshots or HAR files. They may also be tied to a single region or environment, causing compliance issues and unstable tests when passwords change or accounts are locked. This creates both security risk and pipeline noise.
Q3. How do NWB accounts improve security and compliance?
NWB accounts remove real user data from automated runs. Credentials are stored as secrets in the pipeline, injected dynamically, and can be reset between runs. This reduces the chance of exposing sensitive information and helps teams align with data privacy and regulatory requirements.
Q4. What are the main benefits of using NWB accounts in QA?
Teams see fewer credential-related failures, more stable pipelines, consistent test data, and clearer ownership of test runs. NWB accounts also make it easier to test region-specific features safely across multiple environments without relying on individual tester accounts.
Q5. How can a QA team start implementing NWB accounts?
Begin by identifying flows that currently rely on personal credentials, such as login, regional journeys, and sensitive transactions. Create dedicated NWB test accounts per region and environment, store their credentials in a secure vault, wire them into your CI/CD pipeline, and add a reset or cleanup step after each run to keep data consistent.
We Also Provide Training In:
- Advanced Selenium Training
- Playwright Training
- Gen AI Training
- AWS Training
- REST API Training
- Full Stack Training
- Appium Training
- DevOps Training
- JMeter Performance Training
Author’s Bio:

Content Writer at Testleaf, specializing in SEO-driven content for test automation, software development, and cybersecurity. I turn complex technical topics into clear, engaging stories that educate, inspire, and drive digital transformation.
Ezhirkadhir Raja
Content Writer – Testleaf







